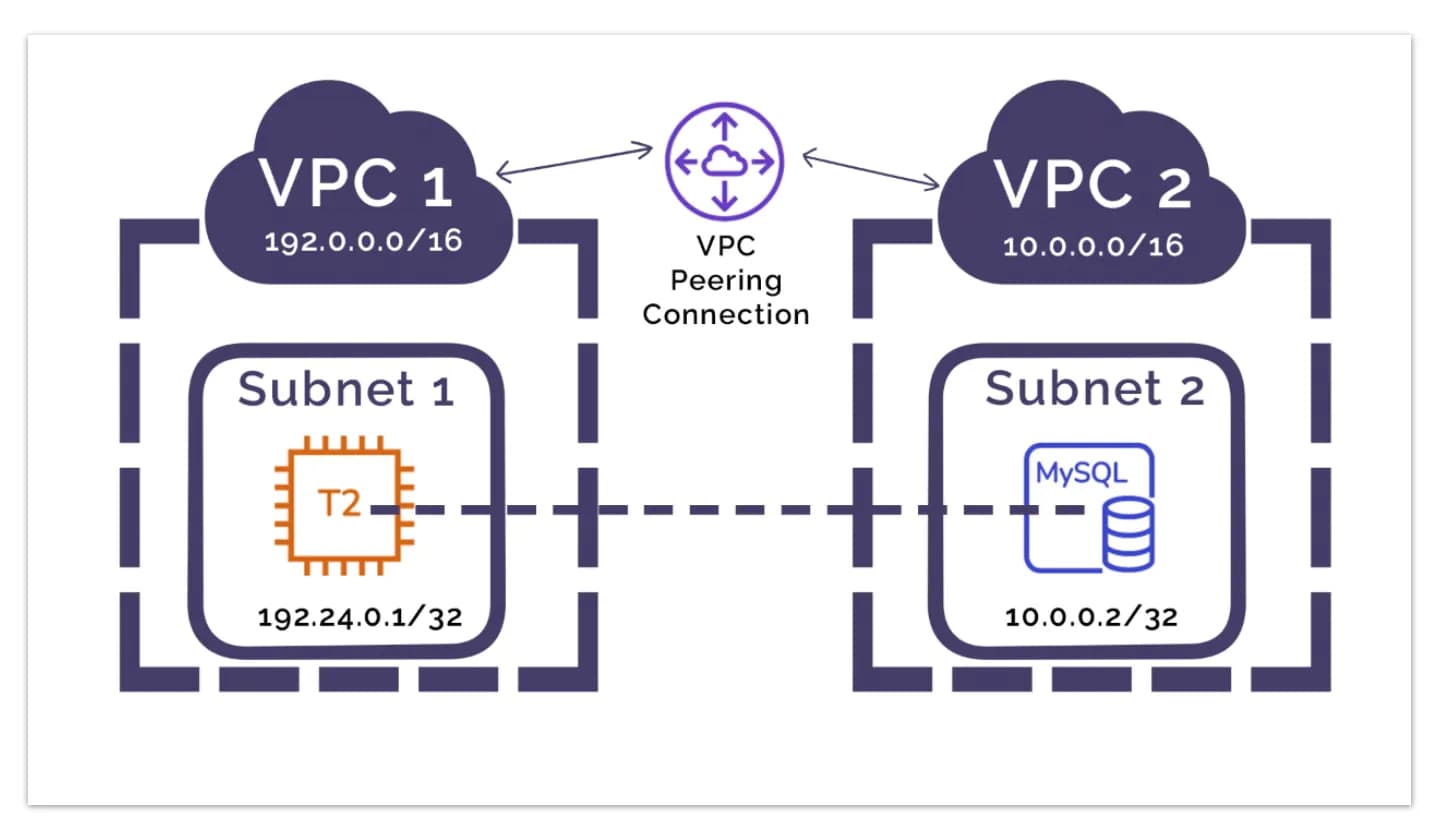
In this article demonstrates how to establish secure communication between EC2 instances residing in private subnets across separate VPCs in AWS. So we will do the following steps:
- Creating VPCs and Private Subnets: We’ll create two VPCs and configure dedicated private subnets within each for secure resource placement.
- Deploying EC2 Instances: We’ll launch EC2 instances within the private subnets, ensuring isolation from the public internet.
- Implementing NAT Gateways and Public Subnets: We’ll set up NAT gateways and public subnets to facilitate outbound internet access for one of the private subnet.
- Installing nginx Server: We’ll install and configure an nginx web server on an EC2 instance in one private subnet.
- VPC Peering and Inter-VPC Communication: We’ll establish VPC peering to connect the two VPCs and demonstrate how to use curl commands to initiate communication between the nginx server in one VPC and an EC2 instance residing in the private subnet of the other VPC.
Table of contents
Open Table of contents
- Creating and Configuring a VPC in AWS
- Launching and Connecting to an EC2 Instance in AWS
- Creating and Configuring a Private Subnet in AWS VPC
- But What is a NAT Gateway?
- Configuring a NAT Gateway for Private Subnet Internet Access:
- Completing the Network Configuration: VPC Peering and Cross-VPC Communication
- What is VPC Peering?
- Reference:
Creating and Configuring a VPC in AWS
When we create a new account in AWS, it automatically attaches a new VPC with the main route table, main network ACL, etc, which is marked as “Yes” in the Default VPC column. So now we will create a new VPC, attaching an internet gateway, creating subnets, and configuring routing for the VPC.
Step 1: Create a VPC
Navigate to the VPC section and click on Create VPC.
- In the Name tag (optional) field, enter a name for your VPC, for example:
MyVPC. - In the IPv4 CIDR block input section, enter:
10.100.0.0/16. - Leave the rest of the settings as they are and click the
Create VPCbutton.
Step 2: Create and Attach an Internet Gateway
- Next go to the Internet Gateways section and click on
Create internet gateway. - Name the internet gateway, for example:
MyVPC_igw, and keep the rest of the settings as they are. And thenClick Create. - After the internet gateway is created, attach it to the newly created VPC by selecting the internet gateway and clicking Attach to VPC. Choose the VPC
MyVPCand save the changes.
Step 3: Create a Subnet
- Now we will create Subnet and for that navigate to the Subnets section and click on
Create subnet. - Select the VPC ID of your newly created VPC (
MyVPC). This will display additional options below. - Set the Subnet name to
MyVPC_Public_subnet. - Select any Availability Zone. Remember, subnets work at the AZ level, so selecting an AZ is mandatory.
- In the IPv4 subnet CIDR block section, enter:
10.100.0.0/24. - Click
Create Subnet.
Step 4: Enable Auto-Assign Public IP
- Select the newly created subnet (
MyVPC_Public_subnet) and go toEdit subnet settings. - Enable the
Auto-assign public IPv4 addressoption and save the changes.
Step 5: Create and Configure a Route Table
- Navigate to the Route Tables section and click on
Create route table. - Set the name as
MyVPC-Publicand choose the VPCMyVPC. - After creating the route table, go to
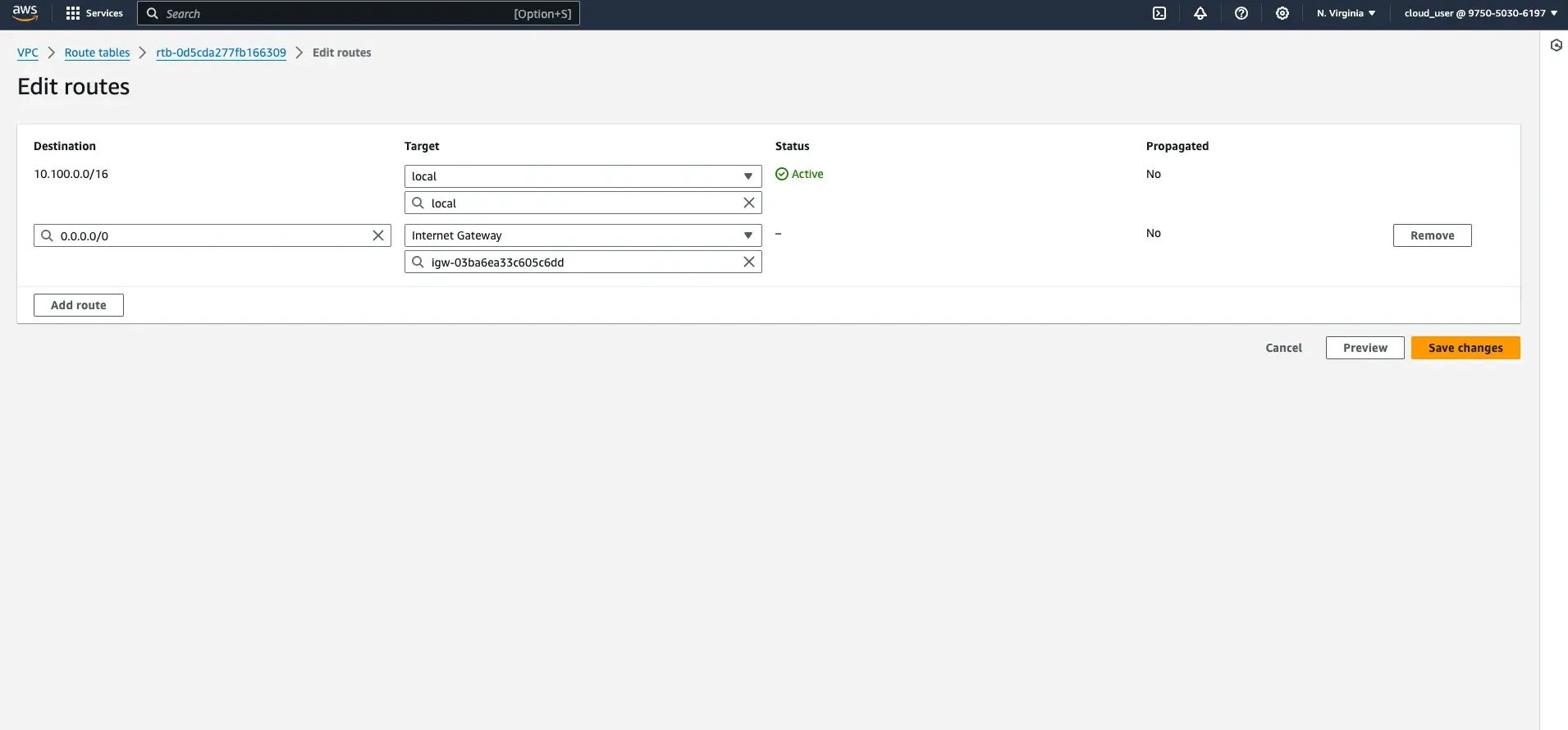
Edit routesand add a new route: - Set the Destination to
0.0.0.0/0. - Set the Target to
Internet Gatewayand select the newly created internet gateway (MyVPC_igw). - Save the changes.
Step 6: Associate the Route Table with the Subnet
- The route table won’t work as expected until it is associated with a subnet.
- Go to the
Subnet associationstab and click onEdit subnet associations. - Select the public subnet (
MyVPC_Public_subnet) and save the changes.
Launching and Connecting to an EC2 Instance in AWS
Now that our network configuration is complete, the next step is to create an EC2 instance and verify connectivity. Follow these steps to launch an EC2 instance and connect to it via SSH from your local machine.
Step 1: Launch an EC2 Instance
- Navigate to the EC2 console.
- Click on Launch Instance.
- In the Network settings section, select your custom VPC (
MyVPC) and the public subnet (MyVPC_Public_subnet). - Complete the remaining instance configuration steps as needed, and then launch the instance.
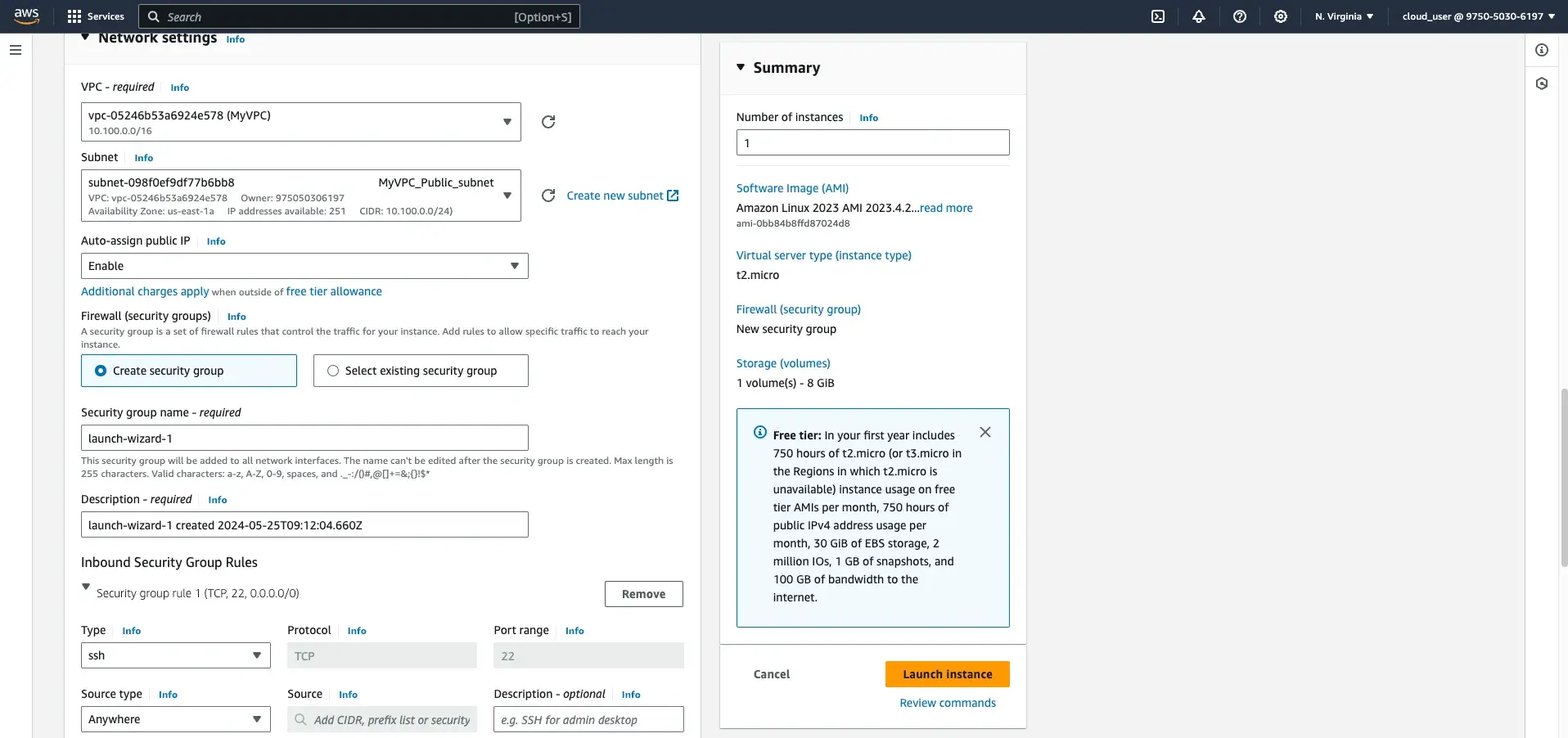
Step 2: Obtain the Public IP and Key Pair
- After launching the instance, select it from the
Instances listto view its details. - Copy the public IP address of the instance.
- Ensure you have the
.pemfile (key pair) downloaded for SSH access. This file is essential for secure remote connections.
Step 3: Set Permissions for the .pem File
On your local machine, set the read permission for the .pem file to ensure secure access:
chmod 400 /path/to/your/pem/file.pemStep 4: Connect to the EC2 Instance via SSH
- Open your terminal or command prompt.
- Use the following command to connect to your EC2 instance:
ssh -i /path/to/your/pem/file.pem ec2-user@<public_ip_address>Creating and Configuring a Private Subnet in AWS VPC
Now, we will create a private subnet within our custom VPC and configure it to restrict direct traffic from the internet.
Step 1: Create a Private Subnet
- Navigate to the Subnets section in the AWS VPC console.
- Select your custom VPC (
MyVPC). - Click on
Create Subnet. - Set the Subnet name to
MyVPC-Private. - Choose an Availability Zone (AZ).
- In the IPv4 CIDR block field, enter
10.100.1.0/24. - Click
Create subnet.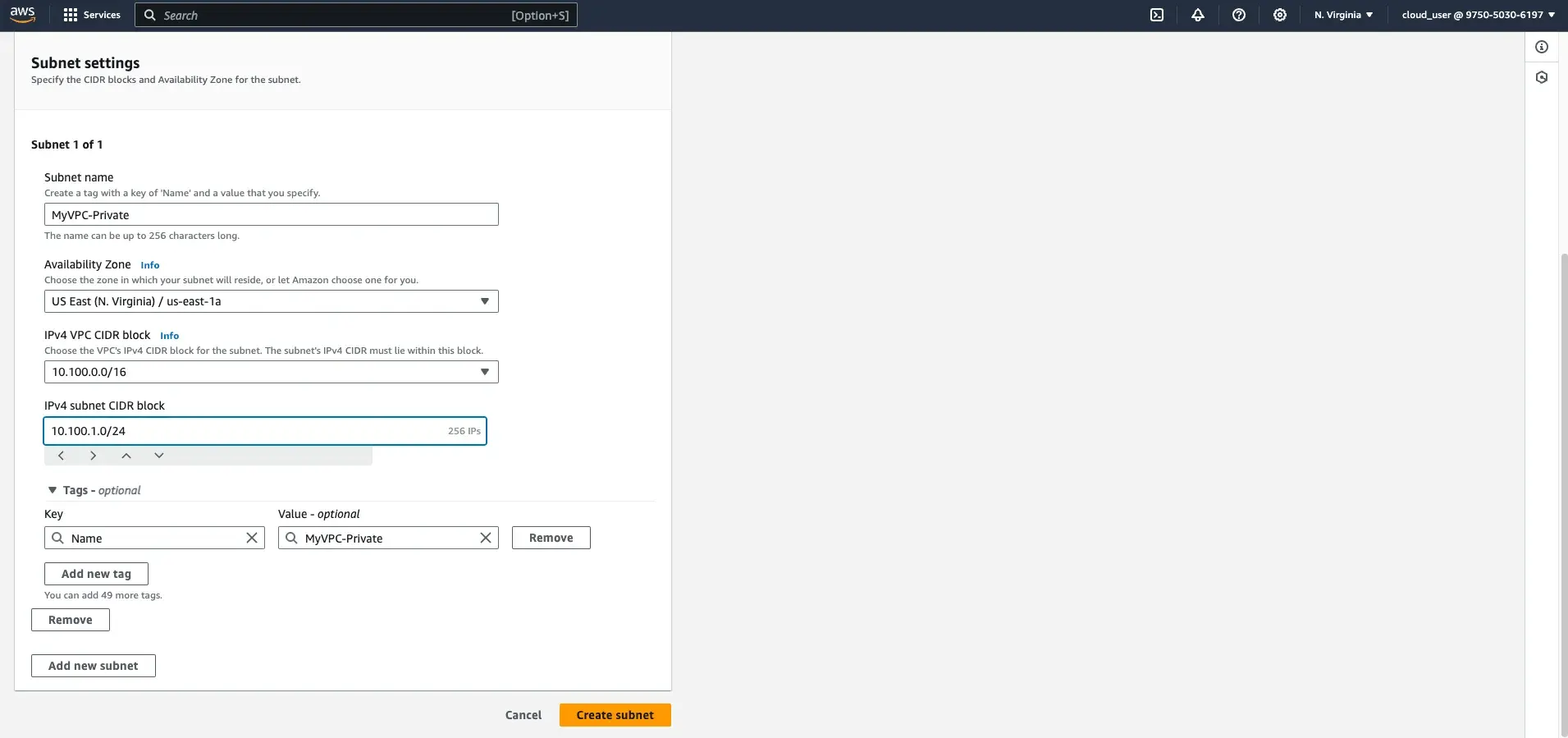
Step 2: Create a Dedicated Route Table for the Private Subnet
- Go to the Route tables section and click on
Create route table. - Name the route table
MyVPC-Private. - Select your custom VPC (
MyVPC) and save. - The default local route will already be associated with this route table, so no additional routes need to be added.
- Attach the private subnet to this route table:
- Go to Subnet associations.
- Select the private subnet (
MyVPC-Private). - Save the changes.
- Verify the route table association by navigating to the Private subnet section, selecting the subnet and checking the
Route tablesection.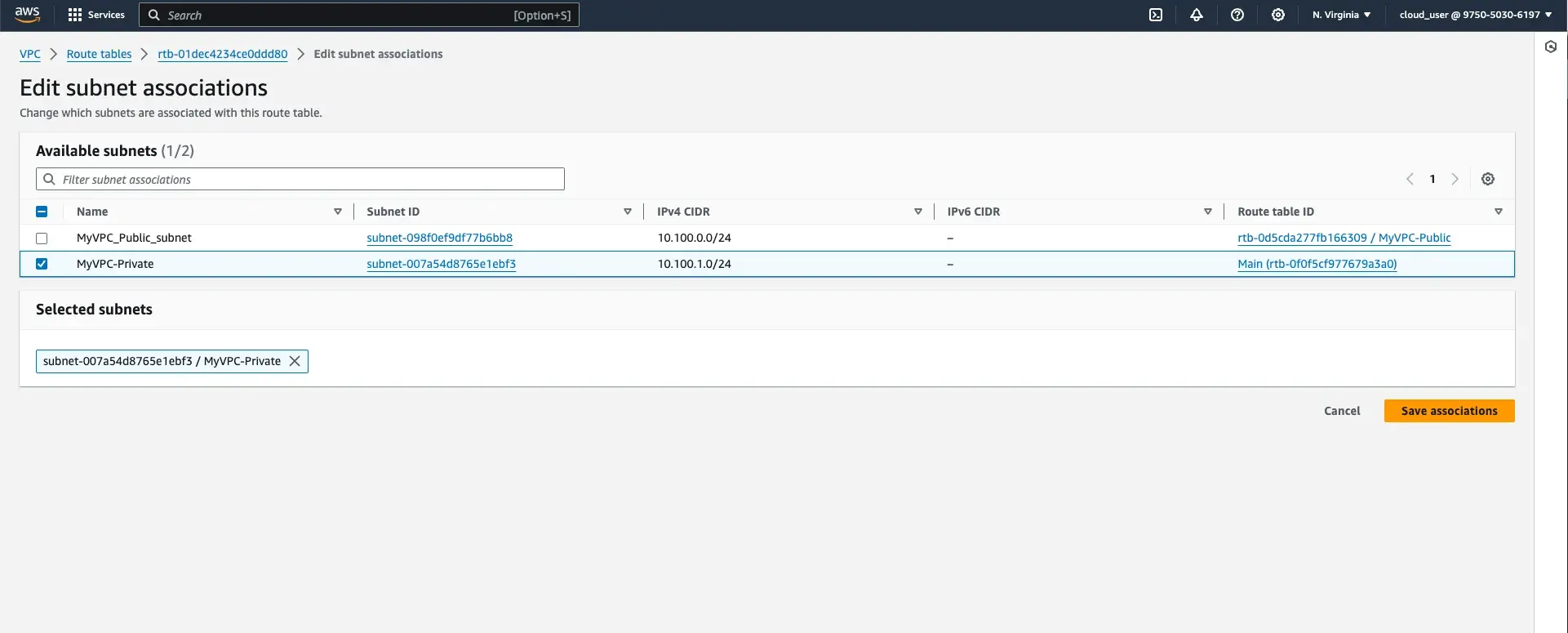
Step 3: Launch an EC2 Instance in the Private Subnet
- Navigate to the EC2 section and click Launch Instance.
- Set the instance name to
EC2-B. - Select the previously saved key pair.
- In the Network settings section, select your custom VPC and the private subnet (
MyVPC-Private). - Disable the Auto-assign public IP option.
- Configure the Inbound Security Group Rules:
- Add an
SSHrule with the Source type set to Custom and the source as the VPC CIDR block (10.100.0.0/16). - Add a rule for
All ICMP - IPv4with the Source type set to Custom and the source as the VPC CIDR block (10.100.0.0/16).
- Add an
- Launch the instance.
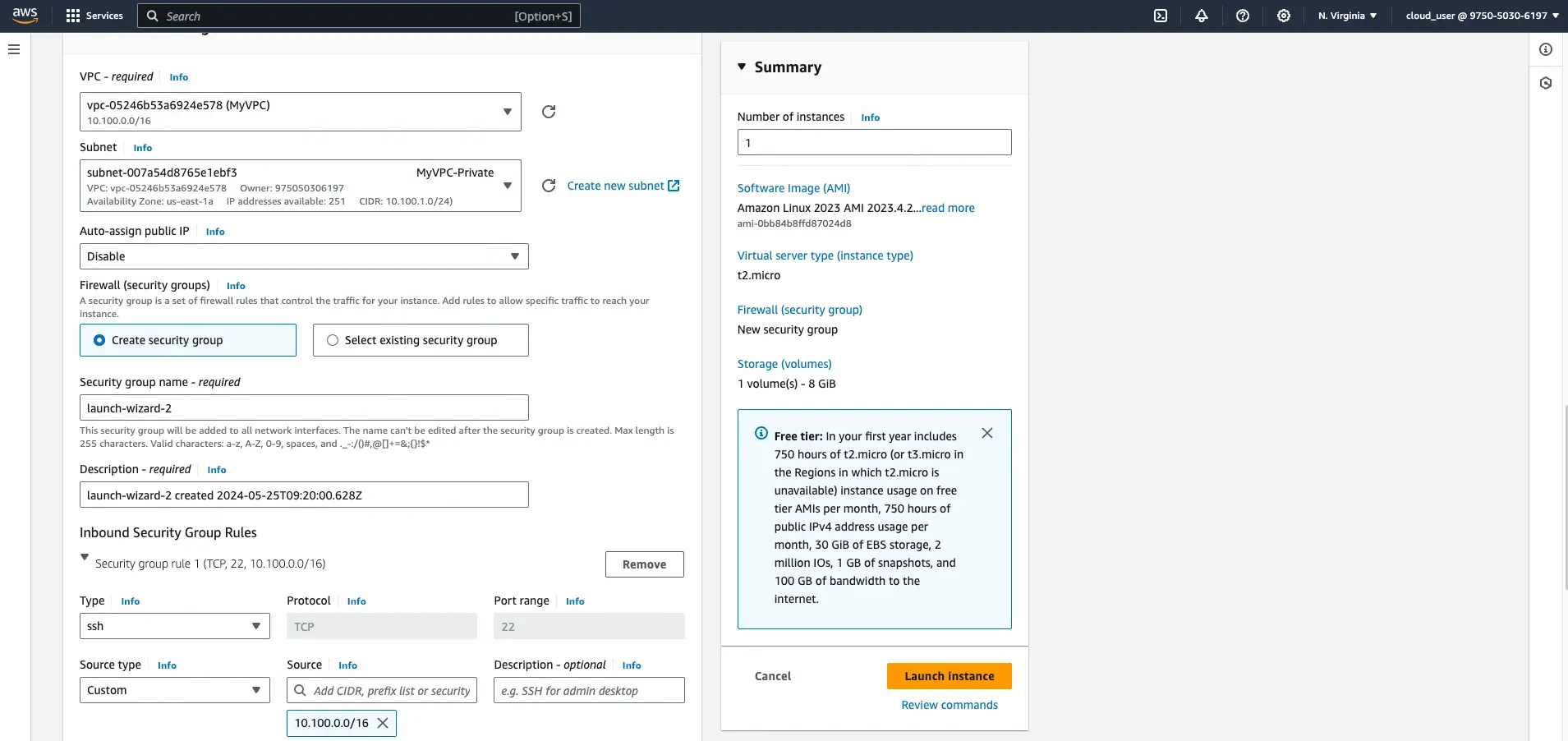
Step 4: Connect to the Private EC2 Instance
To connect to the EC2 instance in the private subnet, we can use SSH tunneling or SSH forwarding. But for simplicity, we will use the following method:
- Copy the key pair file (.pem) from your local machine to the public EC2 instance.
- On the public EC2 instance, create a new
.pemfile and set the appropriate read permissions:
chmod 400 /path/to/key.pem- Obtain the private IP address of the private EC2 instance (
EC2-B). - From the public EC2 instance, connect to the private EC2 instance using SSH:
ssh -i /path/to/key.pem ec2-user@<ip-of-private-ec2-instance>- Test the connectivity by pinging the private EC2 instance:
ping <ip-of-private-ec2-instance>However, if you attempt to ping google.com or any public domain, the request will time out. This is because the private subnet does not have internet access. To enable internet connectivity for instances in the private subnet, a NAT gateway must be configured.
But What is a NAT Gateway?
A NAT(Network Address Translation) gateway allows instances in a private subnet to connect to the internet or other AWS services but prevents the internet from initiating a connection with those instances. Essentially, it translates the private IP addresses of the instances to the public IP address of the NAT gateway, enabling secure outbound internet traffic.
How NAT Works
Here’s a simplified explanation of how NAT works:
- An instance in a private subnet sends an IP packet with its private IP address as the source and the destination address of an external service (e.g.
google.com). - The packet reaches the NAT gateway, which replaces the private IP address with its own public IP address (a process known as source
NATorSNAT). - The NAT gateway forwards the packet to the internet.
- The external service responds to the NAT gateway’s public IP address.
- The NAT gateway receives the response and forwards it back to the original instance in the private subnet.
Setting Up a NAT Gateway
To set up a NAT gateway, follow these steps:
- Create a NAT Gateway:
Launch a NAT gateway in a public subnet. This subnet must have a route to an internet gateway. Allocate an Elastic IP address to the NAT gateway. - Modify Route Tables: Update the route table of the private subnet to direct internet-bound traffic to the NAT gateway.
High Availability and Scalability
NAT gateways are managed by AWS, offering high availability and scalability. They can handle bandwidth from 5 Gbps to 100 Gbps without any manual configuration. However, since a NAT gateway is associated with a specific availability zone (AZ), if the AZ goes down, the instances that rely on that NAT gateway lose internet connectivity. To mitigate this risk, you can create NAT gateways in multiple AZs and configure your route tables accordingly.
Security Considerations
NAT gateways do not have security groups, meaning you cannot directly control the inbound and outbound traffic at the NAT gateway level. Instead, you rely on the Network ACLs (Access Control Lists) applied at the subnet level. These ACLs control traffic in and out of the NAT gateway, ensuring that your security policies are enforced.
Cost Considerations
Using a NAT gateway incurs costs, including an hourly charge and data processing fees. For production environments, AWS-managed NAT gateways are recommended due to their reliability and ease of use. However, for development and testing environments, you might consider using a NAT instance (an EC2 instance configured as a NAT). This can be more cost-effective, although it requires additional management overhead.
Configuring a NAT Gateway for Private Subnet Internet Access:
Now, we will set up a NAT (Network Address Translation) gateway to enable instances in the private subnet to access the internet for outbound traffic.
Step 1: Create a NAT Gateway
- Navigate to the NAT Gateways section in the AWS VPC console.
- Click the Create NAT Gateway button.
- Set the Name to
MyVPC-NATGW. - Select the Public Subnet where the NAT gateway will reside.
- Click on Allocate Elastic IP to assign an Elastic IP to the NAT gateway.
- Save the configuration.
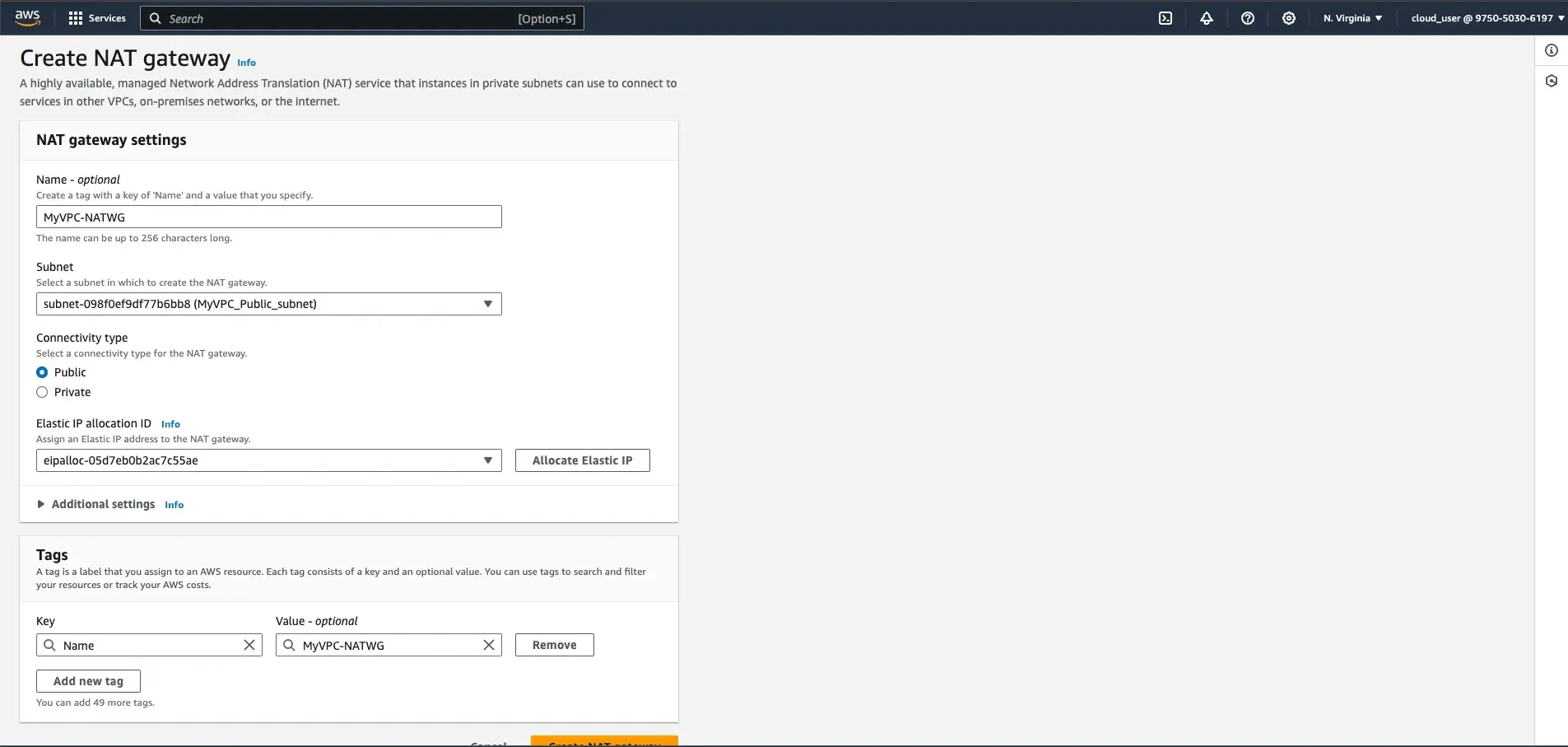
Step 2: Modify the Route Table for the Private Subnet
- Go to the Route Tables section and select the route table associated with your private subnet (
MyVPC-Private). - Click on Edit Routes and then Add Route.
- Set the Destination to
0.0.0.0/0. - For the Target, select the newly created NAT Gateway (
MyVPC-NATGW). - Save the changes.
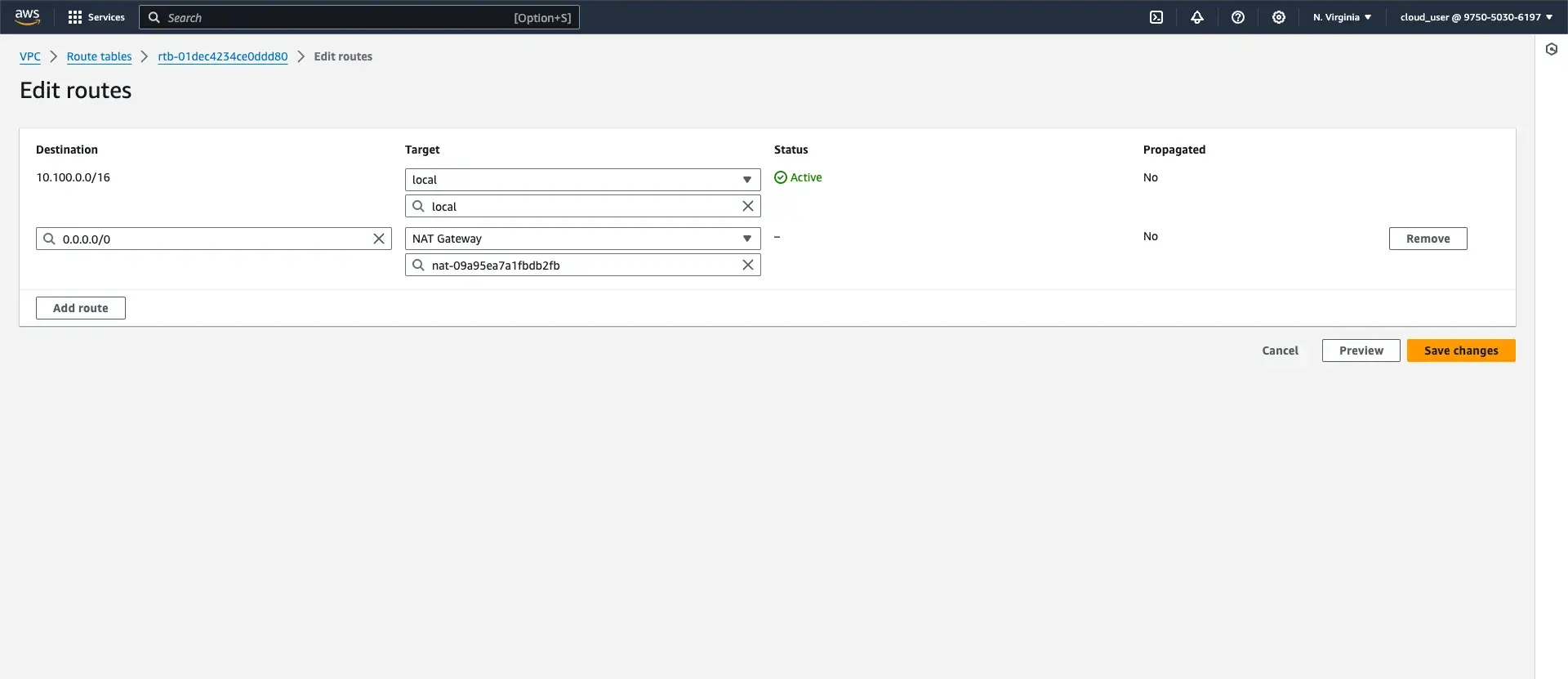
Step 3: Verify the Configuration
- Connect to the EC2 instance in the private subnet (
EC2-B). - Then ping to a public domain:
ping google.com - We will see successful ping responses, indicating that the instance in the private subnet now has internet access for outbound traffic.
Completing the Network Configuration: VPC Peering and Cross-VPC Communication
An essential task still remains to fully configure our network: establishing communication between two VPCs. We will create another VPC with a private subnet, launch an EC2 instance in it, and set up VPC peering to enable communication between instances in different VPCs. Additionally, we will install Nginx on an instance in the first VPC and verify that it can be accessed from an instance in the second VPC.
What is VPC Peering?
From amazon doc: A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. The VPCs can be in different Regions (also known as an inter-Region VPC peering connection).
Let’s jump right in with a hands-on activity to understand this:
Step 1: Create a Private Subnet in the Second VPC
- Create the Second VPC:
- Navigate to the VPC section in the AWS Management Console and click Create VPC.
- Name the VPC
VPC-TWO. - Set the IPv4 CIDR block to
10.200.0.0/16. - Leave the rest of the settings as default and click Create VPC.
- Create a Private Subnet in the Second VPC:
- Go to the Subnets section and click Create subnet.
- Select
VPC-TWOas the VPC ID. - Name the subnet
VPC-TWO-Private. - Choose an Availability Zone.
- Set the IPv4 subnet CIDR block to
10.200.1.0/24. - Click Create Subnet.
- Create a Route Table for the Private Subnet:
- Go to the Route Tables section and click Create route table.
- Name the route table
VPC-TWO-Private. - Select
VPC-TWOas the VPC. - Click Create.
- Go to Subnet associations, click Edit subnet associations, and select
VPC-TWO-Private. - Save the changes.
Step 2: Launch an EC2 Instance in the Private Subnet
- Go to the EC2 section and click Launch Instance.
- Name the instance
EC2-Two-Private. - Select the key pair you want to use.
- In the Network settings, select
VPC-TWOandVPC-TWO-Private. - Disable Auto-assign public IP.
- In the Inbound Security Group Rules section, add the following rules:
- SSH: Set the source to the CIDR block of the first VPC (
10.100.0.0/16). - ICMPv4: Set the source to the CIDR block of the first VPC (
10.100.0.0/16).
- SSH: Set the source to the CIDR block of the first VPC (
- Click Launch Instance.
Step 3: Set Up VPC Peering
- Create a VPC Peering Connection:
- Go to the VPC Peering Connections section and click Create Peering Connection.
- Name the connection MyVPC-Peering.
- Select the first VPC (
VPC-ONE) as the Requester VPC. - Select the second VPC (
VPC-TWO) as the Accepter VPC by copying the VPC ID fromVPC-TWO. - Click Create Peering Connection.
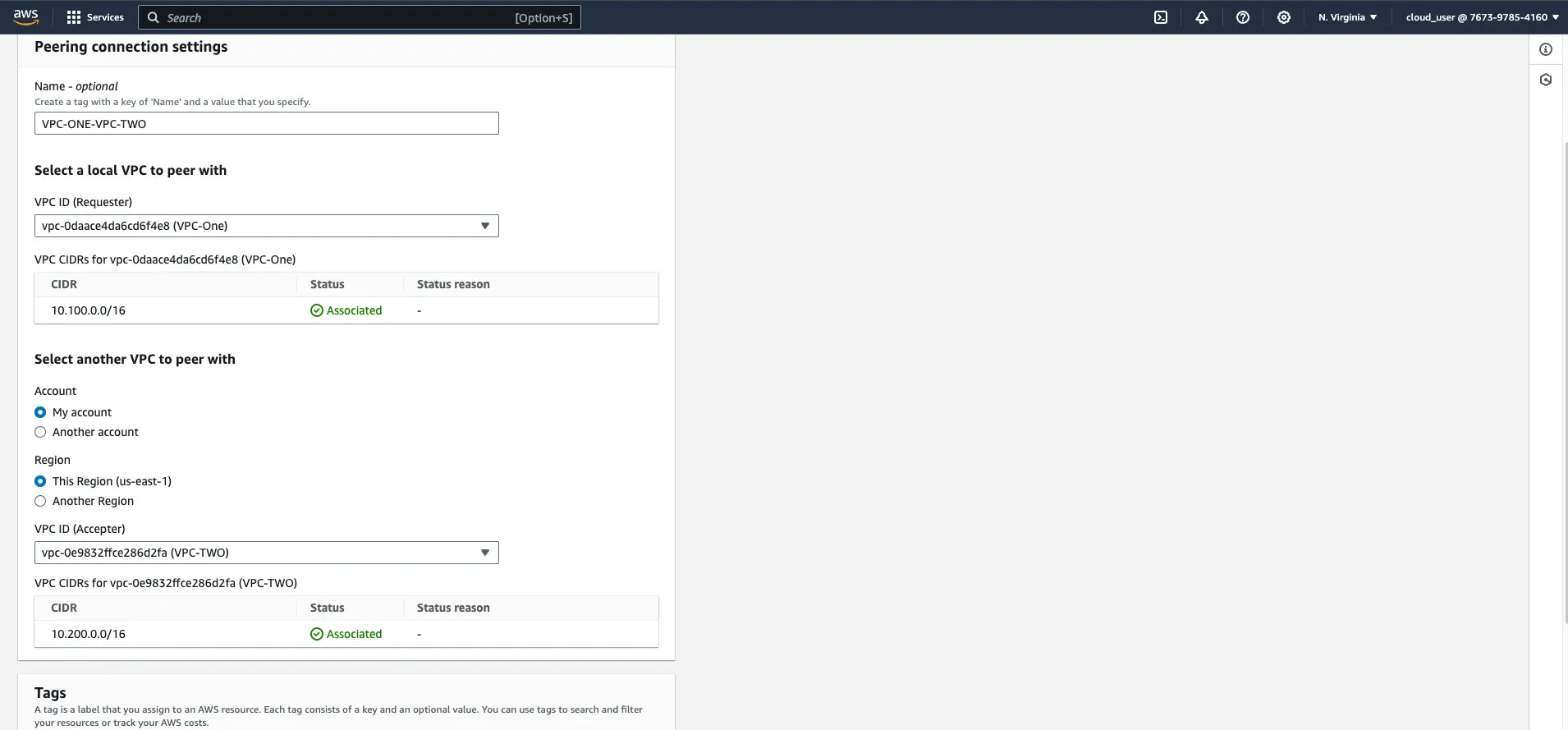
- Accept the Peering Request:
- Navigate to the Peering Connections section in the second VPC’s account.
- Select the peering connection request.
- Click Actions and select Accept Request.
- Confirm that the status is Active.
- Update Route Tables for VPC Peering:
- For the first VPC (
VPC-ONE):- Go to the Route Tables section and select the route table associated with
VPC-ONE-Private. - Click Edit Routes and Add Route.
- Set the Destination to
10.200.0.0/16. - Set the Target to the VPC peering connection (
MyVPC-Peering). - Save the changes.
- Go to the Route Tables section and select the route table associated with
- For the second VPC (
VPC-TWO):- Go to the Route Tables section and select the route table associated with
VPC-TWO-Private. - Click Edit Routes and Add Route.
- Set the Destination to
10.100.0.0/16. - Set the Target to the VPC peering connection (
MyVPC-Peering). - Save the changes.
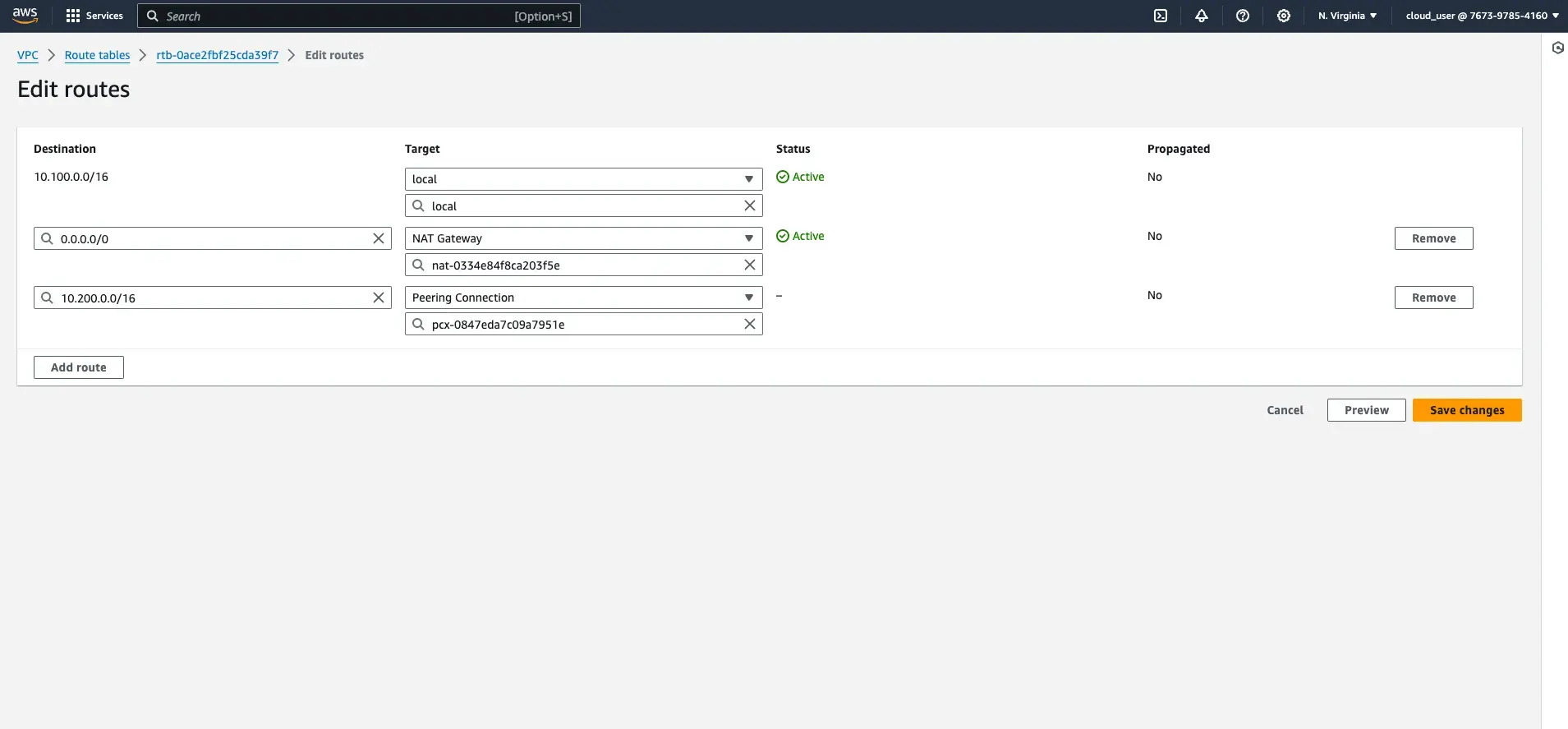
- Go to the Route Tables section and select the route table associated with
Step 4: Configure Security Groups and Test Connectivity
- Configure Security Groups for the First VPC:
- Go to the Security Groups section.
- Select the security group associated with EC2-ONE-Private in VPC-ONE.
- Add an inbound rule to allow HTTP traffic on port 80 from the CIDR block of the second VPC (10.200.0.0/16).
- Save the changes.
- Install Nginx on the EC2 Instance in the First VPC:
- SSH into the EC2 instance in the first VPC’s private subnet.
- Install Nginx using the following commands:
sudo yum update -y
sudo yum install nginx -y
sudo systemctl start nginx
sudo systemctl enable nginx- Test Cross-VPC Communication:
- SSH into the EC2 instance in the second VPC’s private subnet.
- Run the following command to test the connection to the Nginx server:
curl http://10.100.1.208:80 - You should see the Nginx welcome page, indicating successful communication between the instances in different VPCs.
So, by following these steps, we can successfully configured VPC peering and established cross-VPC communication. That’s it! Happy networking.